SSO - ADFS
How to setup ADFS as your Identity Provider
Enable Forms Authentication in ADFS
Forms Authentication must be enabled within ADFS for it to generate a SAML assertion to your digital workplace. For more information about Forms Authentication, Configure the AD FS server for claims-based authentication (Microsoft).
1. Log on to the ADFS server with Administrator credentials
2. Open the ADFS management console and select Authentication Policies
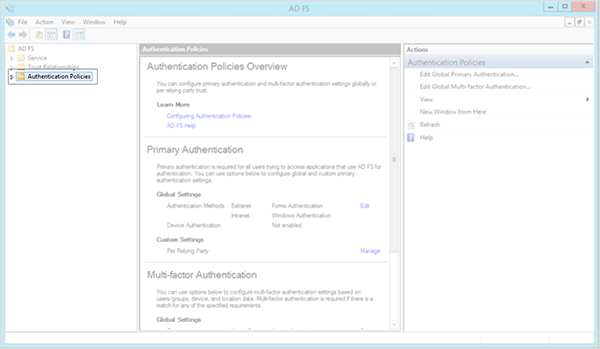
3. Click the Edit link associated with Authentication Methods
While on the Authentication Policies page this link can be found under the following section: Primary Authentication -> Global Settings -> Authentication Methods.
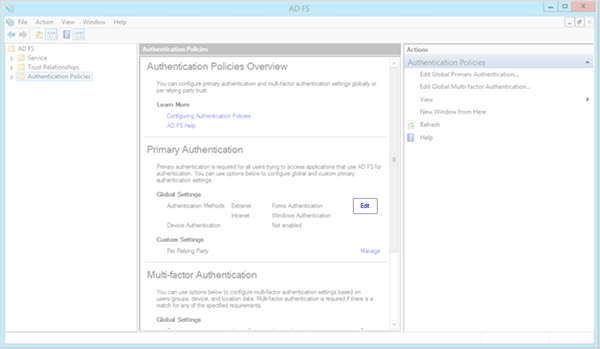
4. Under the Intranet section, verify that Forms Authentication has been enabled
If there is no check in the box next to Forms Authentication it has not been enabled. Click the box to enable this setting. Click the Apply button located at the bottom of the window to have this change take effect.
Create a Relying Party Trust in ADFS
A Relying Party Trust is required to allow ADFS to identify your workplace as a resource partner organization. For more information, see Create a Relying Party Trust (Microsoft).
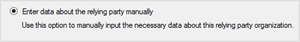
1. On the Select Data Source page in ADFS, select the option Enter data about the relying party manually
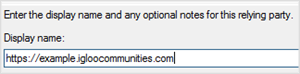
2. On the Specify Display Name page, enter the workplace URL as the Display Name
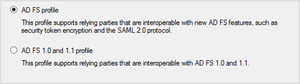
3. On the Choose Profile page, select the ADFS Version to use
If you are using Windows 2003 or older select ADFS 1.0 and 1.1, otherwise use the default which is ADFS profile.
4. On the Configure Certificate page, click next
The assertion must be unencrypted.
5. On the Configure URL page, select Enable support for the SAML 2.0 WebSSO
If there is no check in the box next to Enable support for the SAML 2.0 WebSSO it has not been enabled. Click the box to enable this setting.
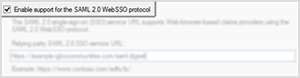
6. Still on the Configure URL page, enter your workplace's SAML endpoint URL in the text field Relying party SAML 2.0 SSO service URL
This will always take the form:
http://{your workplace URL}/saml.digest
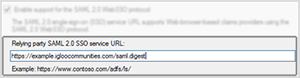
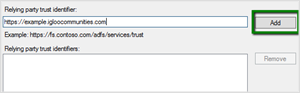
7. On the Configure Identifiers page, enter your workplace's SAML endpoint URL as the Relying party trust identifier
This will always take the form:
http://{your workplace URL}/saml.digest
8. On the Choose Issuance Authorization Rules page, select Permit all users to access the relying party
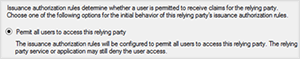
9. Review the settings, and click Finish
Clicking finish will automatically open the claim rules area. This is typically the next step of setting up ADFS as your Identity Provider.
Create Claim Rules in ADFS
Claim Rules control what information is passed in the SAML assertion to your workplace. These must pass name, last name, email and nameID values. For more information, see Configure the AD FS server for claims-based authentication (Microsoft).
1. Select the Edit Claim Rules option found in ADFS, and then click Add Rule
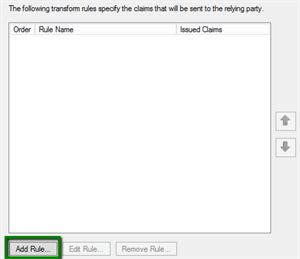
2. Select the rule template Send LDAP Attributes as Claims
3. Give the rule a name
4. Select the Active Directory (AD) as the attribute store
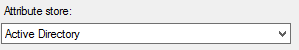
5. Map AD attributes to outgoing claims
The LDAP attribute dropdown will allow the selection of specific attributes within the AD, map them to the outgoing claim. For optimal results, provide the following mappings:
- Given-Name to FName
- Surname to LName
- Email Addresses to Email
- Email Addresses to NameID
Click Finish to create these claims.
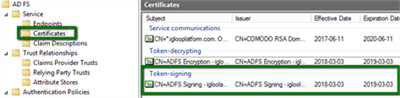
Where to find Signing Token / X.509 Certificate
A connection requires an AD FS token-signing certificate that's passed in the assertion. This certificate is also referred to as the X.509 Certificate. To find this certificate within AD FS, navigate to Service and select Certificates. Download the Token-signing certificate and open it in a text editor to view it. For more information, see ADFS Certificates - SSL, Token Signing, and Client Authentication Certs (Microsoft).
Workplace Configuration
General information about your workplace's SAML configuration page can be found in our article SSO - SAML Authentication.
1. Select the Sign In Settings page from the Site Control Panel
2. Click the Configure SAML Authentication link

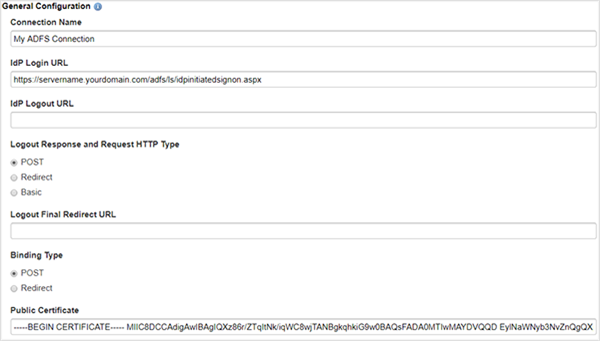
3. Complete the General Configuration fields
Connection Name: Mandatory field that is used to identify the connection. IdP Login URL: The ADFS login URL will typically follow the structure below.
https://servername.yourdomain.com/adfs/ls/idpinitiatedsignon.aspx
IdP Logout URL: This is the URL to which your site will send logout information. This URL will typically follow the structure below.
https://servername.yourdomain.com/adfs/ls/idpinitiatedsignon.aspx/?wa=wsignout1.0
Logout Response and Request HTTP Type: Select Basic.
Logout Final Redirect URL: Enter a URL for your IDP to redirect users to after logout has been completed.
Binding Type: Select Post.
Public Certificate: Copy the certificate that was downloaded in the Where to find Signing Token / X.509 Certificate section of this document.
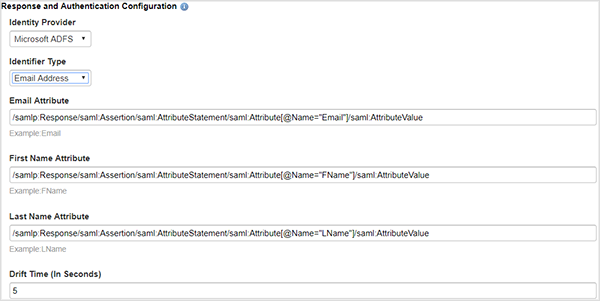
4. Complete the Response and Authentication Configuration fields
Identity Provider: Select Microsoft ADFS from the dropdown menu.
Note: If you are using ADFS 4.0, select Other as the Identity Provider. Change the Identifier Path to:
/samlp:Response/saml:Assertion/saml:AttributeStatement/saml:Attribute[@Name="NameID"]/saml:AttributeValue
You can then change the Identity Provider back to Microsoft ADFS.
Identifier Type: Select Email Address. This assumes that the NameID value has been set to Email Addresses, as described in Step 5 of the Create Claim Rules in ADFS instructions found above.
Attributes: These attributes should match the ADFS mapped claims. Based on Step 5 of the Create Claim Rules in ADFS instructions found above, these would be:
/samlp:Response/saml:Assertion/saml:AttributeStatement/saml:Attribute[@Name="Email"]/saml:AttributeValue
/samlp:Response/saml:Assertion/saml:AttributeStatement/saml:Attribute[@Name="FName"]/saml:AttributeValue
/samlp:Response/saml:Assertion/saml:AttributeStatement/saml:Attribute[@Name="LName"]/saml:AttributeValue
Drift Time: This can be left at its default time of 5 seconds. For troubleshooting, this value can be increased if there is concern that network latency could be causing authentication issues.
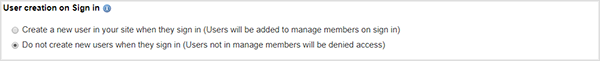
5. Enable/Disable SAML provisioning of new members
Select how your digital workplace handles users who attempt to sign in to your digital workplace when they have valid credentials but are not members of the workplace.
If your digital workplace uses the ILST to manage members, select Do not create new users when they sign in to avoid the creation of duplicate user accounts.
6. Set how members navigate to the SSO sign in page
Use SAML button on "Sign in" screen: Adds a SSO sign in button to the Igloo Authentication page.
Redirect all users to IdP: Automatically redirects members to your ADFS sign in page if they attempt to access the workplace without an existing session.
